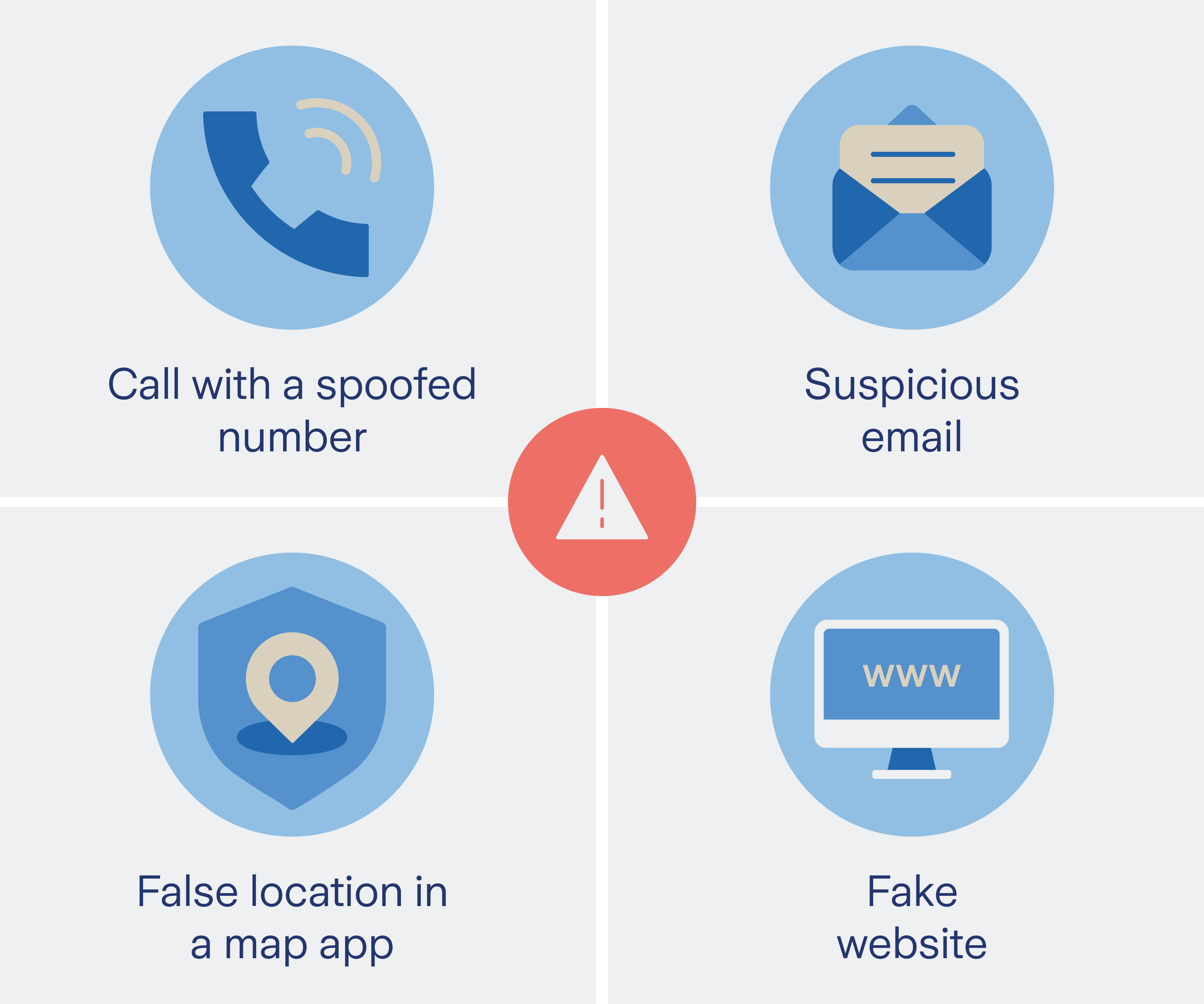
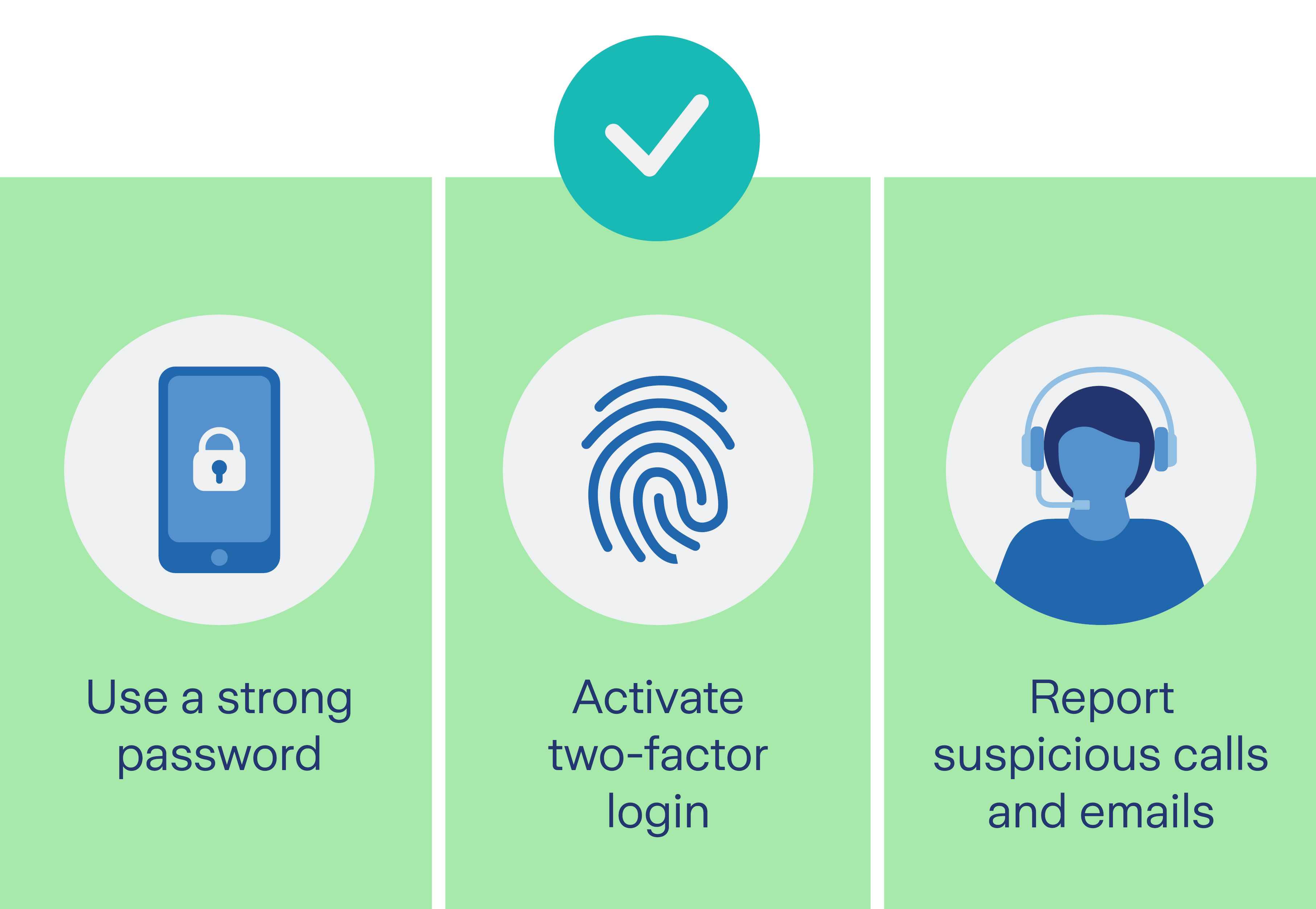
Spoofing: fake identities as a method of fraud
You're leisurely drinking your coffee in the morning. With a quick glance at your cell phone before the day really begins. A new SMS appears: Your bank is getting in touch because there has allegedly been unusual access on your account. You feel uneasy – better react immediately. You click on the link and enter your details to protect your account. But in reality, fraudsters are behind it all. Spoofing is the name given to this perfidious scam in which criminals deliberately use false identities to obtain your confidential information.